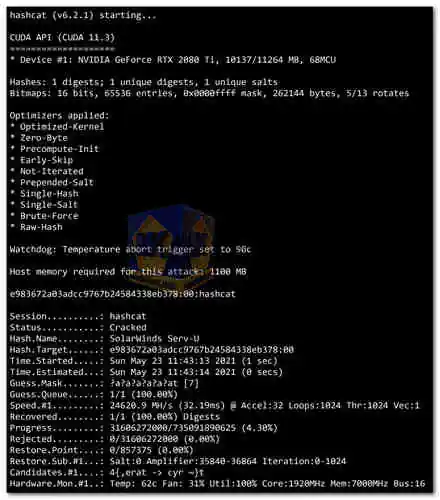
Hashcat stands as the world's fastest and most advanced password recovery utility, designed to crack passwords hashed with over 300 highly-optimized algorithms. Offering unparalleled speed and efficiency, Hashcat supports a myriad of attack modes and works seamlessly across various operating systems and hardware configurations...
Hashcat Key Features:
- World's Fastest Password Cracker: Hashcat has earned its reputation as the fastest password cracker globally, leveraging cutting-edge techniques to achieve remarkable speeds in password recovery.
- In-Kernel Rule Engine: Pioneering in-kernel rule engine sets Hashcat apart, providing an unprecedented level of flexibility and efficiency in crafting and applying password-cracking rules.
- Free and Open-Source: Hashcat is freely available under the MIT License, emphasizing its commitment to accessibility and collaboration within the security community.
- Multi-OS and Multi-Platform Support: Hashcat is compatible with Linux, Windows, and macOS, offering a versatile solution that works across different operating systems and platforms, including CPU, GPU, APU, and more.
- Multi-Hash and Multi-Device Capabilities: Hashcat excels in cracking multiple hashes simultaneously, utilizing multiple devices within the same system, and supporting a mix of device types for enhanced performance.
- Distributed Cracking Networks: Facilitating collaborative efforts, Hashcat supports distributed password cracking networks, enabling users to harness the power of multiple systems for efficient password recovery.
- Interactive Pause/Resume, Sessions, and Restore: Users can interactively pause and resume operations, and Hashcat provides support for sessions and restore functionality, ensuring flexibility and convenience in handling complex cracking tasks.
- Flexible Input Sources: Hashcat supports reading password candidates from files and stdin, offering versatility in input sources to accommodate different workflows.
- Hex-Salt and Hex-Charset Support: With support for hex-salt and hex-charset, Hashcat enhances its flexibility in handling diverse password hashing scenarios.
- Automatic Performance Tuning and Keyspace Ordering: Hashcat streamlines the cracking process with automatic performance tuning and keyspace ordering through markov-chains, optimizing the efficiency of password recovery.
- Built-In Benchmarking System and Thermal Watchdog: Users can assess the performance of their hardware with Hashcat's built-in benchmarking system, and an integrated thermal watchdog ensures stability during extended operations.
- Extensive Hash-Type Support: Hashcat supports over 350 hash types, demonstrating its commitment to compatibility and performance across a wide range of security protocols.
- Installation: Installation is straightforward. Users can unpack Hashcat in their desired location, ensuring full file paths remain intact by using the '7z x' command when unpacking the archive from the command line.
Attack Modes:
Hashcat offers five distinct attack modes:
- Straight, Combination, Brute-force, Hybrid dict + mask and Hybrid mask + dict.
- Additionally, it supports Association attack mode and seamlessly integrates rule acceptance.
Supported Compute Runtimes and Device Types:
Hashcat supports a variety of compute runtimes and device types, ensuring compatibility with different hardware configurations:
- AMD OpenCL, ROCm.
- Apple OpenCL, Metal.
- Intel OpenCL.
- NVIDIA OpenCL, CUDA.
- POCL OpenCL.
- Supported device types include GPU, CPU, and APU.
Hashcat's unparalleled speed, comprehensive feature set, and broad compatibility make it an indispensable tool for security professionals, penetration testers, and enthusiasts engaged in password recovery and hash cracking. Its commitment to open-source principles, along with continuous updates and a vibrant community, solidify Hashcat's position as the go-to solution for tackling diverse password cracking challenges.
Hashcat - Changelog.
How to use Hashcat:
Using Hashcat involves several steps, and it requires familiarity with the command-line interface.
Below is a general guide on how to use Hashcat for password cracking:
Prerequisites:
- Install Hashcat: Download (Link below) the latest version of Hashcat. Extract the downloaded file to the desired location.
- Gather Hashes: - Obtain the hash values you want to crack. These can be from password files, databases, or other sources.
Basic Usage:
1. Choose Attack Mode:
Hashcat supports various attack modes. Common ones include:
- Straight: Traditional brute-force attack.
- Dictionary: Uses a wordlist or dictionary file.
- Hybrid: Combines a dictionary with brute-force or mask attacks.
- Brute-force: Tries all possible combinations.
2. Select Hash Type: Specify the hash algorithm used in the target hashes (e.g., MD5, SHA-256).
3. Prepare Wordlists: For dictionary attacks, you need a wordlist. Hashcat supports custom and pre-existing wordlists.
4. Run Hashcat:
- Open a command prompt or terminal window.
- Navigate to the Hashcat directory.
5. Construct Command:
- Build the Hashcat command, specifying the attack mode, hash type, wordlist, and other parameters.
- Example Command: `hashcat -m 0 -a 0 hashes.txt wordlist.txt`
6. Start the Attack:
- Execute the command to begin the password cracking process.
- Hashcat will display progress and any recovered passwords.
Advanced Features:
- Rules: Hashcat supports rules to modify wordlists and enhance the chances of success. Use the `-r` option to specify a rule file.
- Mask Attacks: For brute-force attacks, you can define a mask to guide the search. Use the `-a 3` option and specify the mask.
- Performance Tuning: Hashcat has options for tuning performance automatically (`--optimize`) or manually (`-w` for workload profile).
- Pause and Resume: Hashcat supports interactive pause and resume using the `--restore` option.
- Benchmarking: Evaluate your system's performance with benchmarking using the `-b` option.
Example Commands:
- Dictionary Attack:
hashcat -m 0 -a 0 hashes.txt wordlist.txt - Brute-force Attack with Mask:
hashcat -m 0 -a 3 hashes.txt ?d?d?d?d?d?d - Hybrid Attack:
hashcat -m 0 -a 6 hashes.txt wordlist.txt ?d?d?d?d?d?d
Notes:
- Replace `hashes.txt` with the path to your hash file.
- Adjust hash mode (`-m`) and attack mode (`-a`) based on your specific needs.
- Refer to Hashcat documentation for a comprehensive list of options and advanced features.
Remember to comply with ethical standards and legal regulations when using Hashcat or any password-cracking tool. Unauthorized use is strictly prohibited.